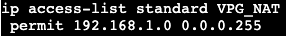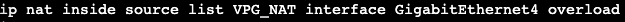- Python Requests Library:
Authentication to vManage requires URL, username/’j_username’, password/’j_password’, ‘j_security_check’, and a session setup via token. The requests library can handle storing the token in a session for further GET requests.
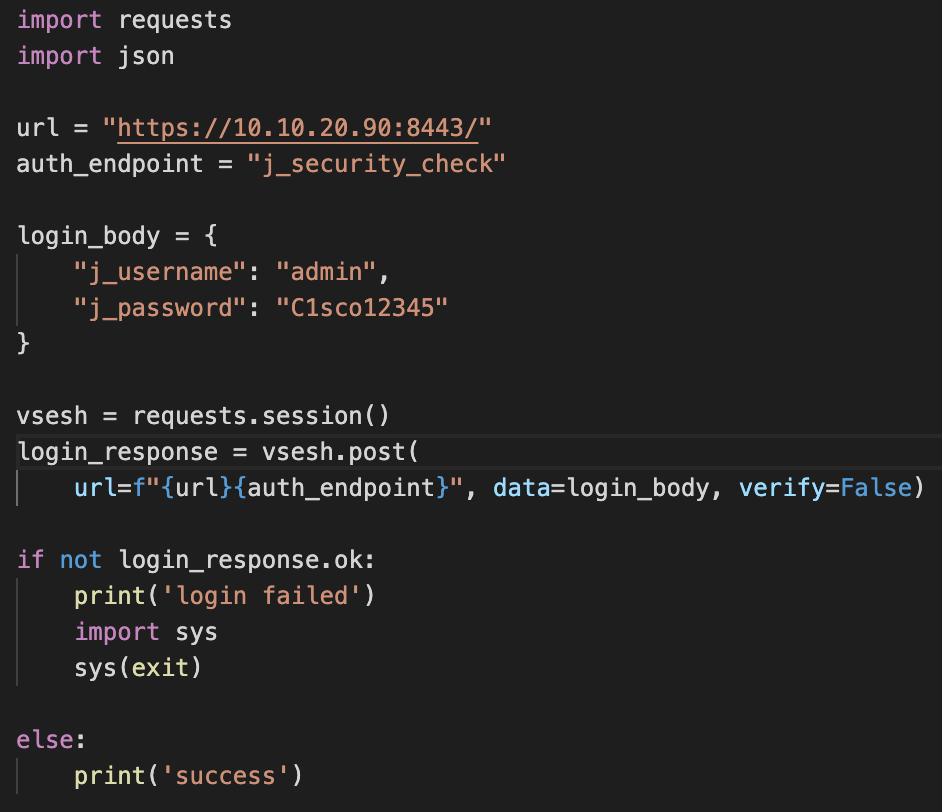
The bottom is an if else statement printing to screen whether the authentication was successful.
Once authentication is successful, the additional URL string can be added to gather information from vManage with the below code. The session, called vsession, will continue being used with a get (.get).
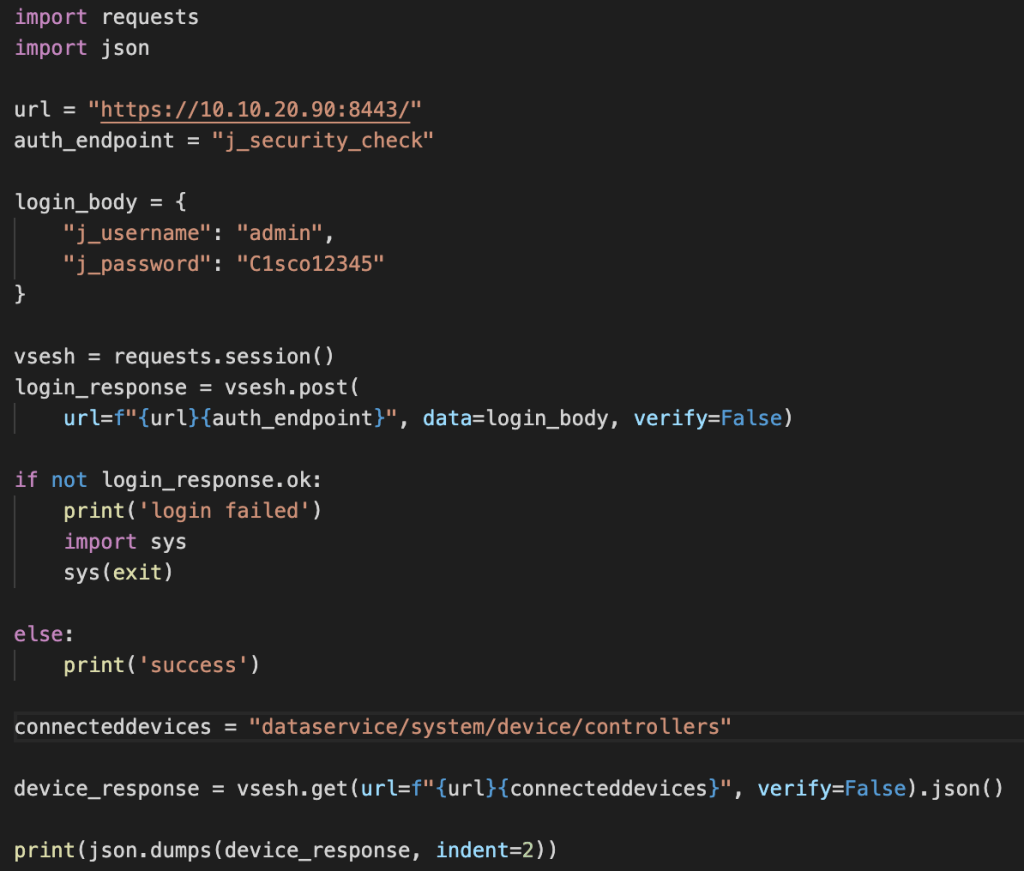
The device_response parameter has .json added to the end so that the data we’re getting back from vManage is in JSON. In addition, we’re using the json.dumps function to print the data on screen in JSON.
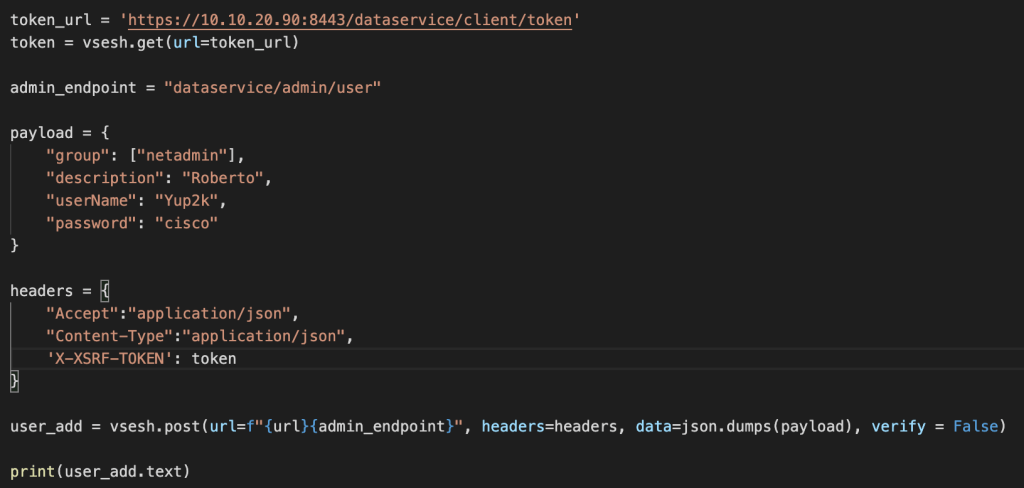
vManage firmware 19.2 moved towards requiring a token for each PUT/POST/DELETE request. Adding the token can be completed by requesting at the URL and adding to headers per below:
token_url = ‘https://<ip/fqdn>:8443/dataservice/client/token’
token = vsesh.get(url=token_url)
headers = {‘X-XSRF-TOKEN’: token}
A post example of adding a new user account named ‘Yup2k’ is in the below image.
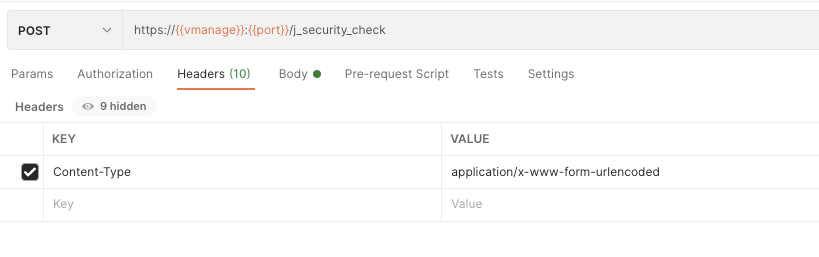
Accessing the vManage API with Postman requires specific authentication parameters. Parameters are listed below:
Under Body:
Radio button x-www-form-urlencoded needs to be selected.
Key – j_username – Value – username
Key – j_password – Value – password
Under Headers:
Key – Content-Type – Value – application/x-www-form-urlencoded

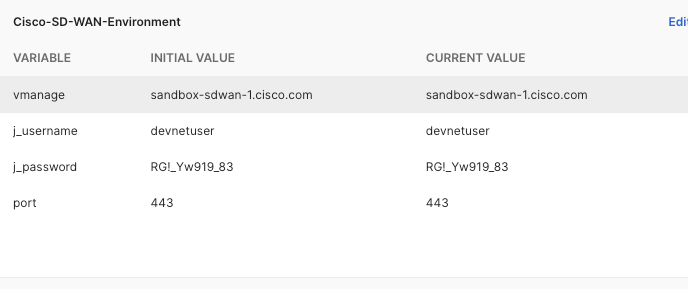
The last image above is a Postman environment setup, which will make interacting with the API via Postman faster.
The initial call needs to be a POST to the API endpoint <vmanage url>:<port>/j_security_check. Once this has been successful, additional calls gathering information or changing configuration can be completed.
Something to be aware of are cookies. A cookie can sit in Postman and expire after a while. If the message received after authentication is HTTP Method Post is not supported by this URL, try going into Cookies and deleting all of them.
For API endpoint information (specifically for Monitoring Endpoints and Configuration Endpoints), the documentation can be found here – https://developer.cisco.com/docs/sdwan/#!introduction .