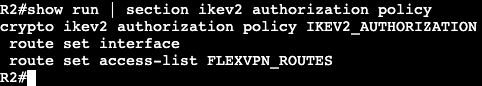
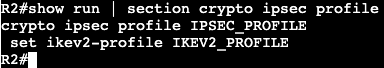
- Port ACLs
- Applies to layer 2 switchports
- Apply ingress only
- Filter transit traffic.
- Traffic ingress on the VLAN/port
- Could be IP or MAC based.
- MAC ACLs only affect non-IP traffic.
- Routed ACL
- Same as PACL but only apply to L3 traffic.
- Apply to L3 ports or SVIs.
- Ingress or Egress unlike PACL
- Can only filter using IPv4 standard/extended ACLs.
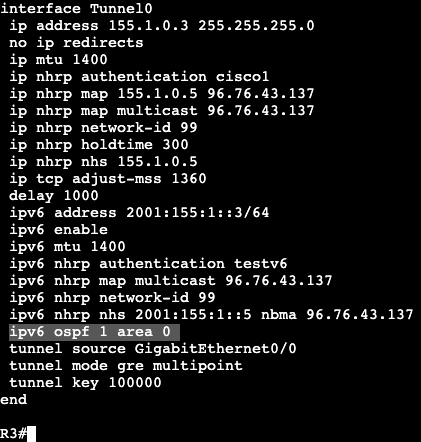
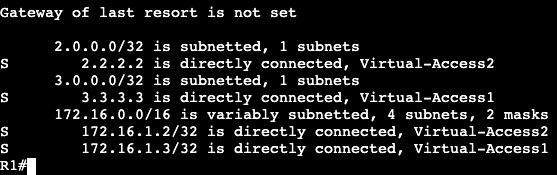
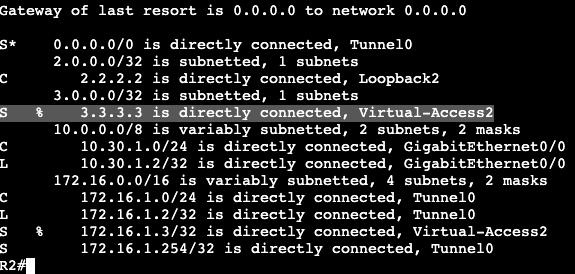
Routed ACL example:

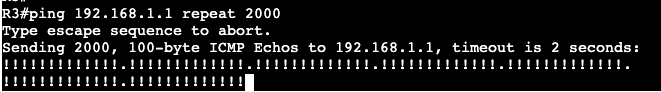
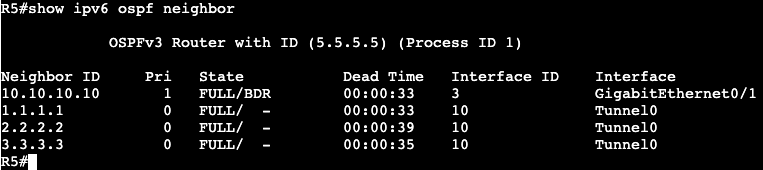
Both switches are running SVI VLAN 10 attached to Gig0/0 as trunk. Each can ping each other’s IP address:
SW1 – 10.10.10.21/16
SW2 – 10.10.10.22/16
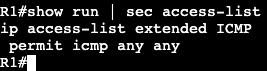
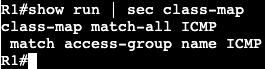
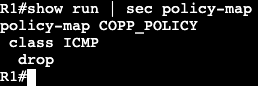
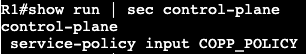
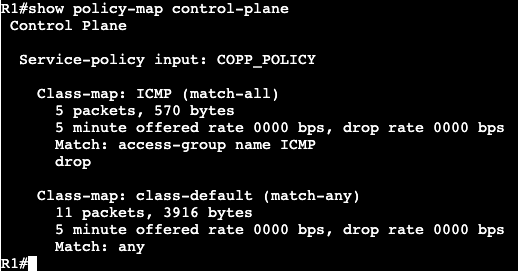
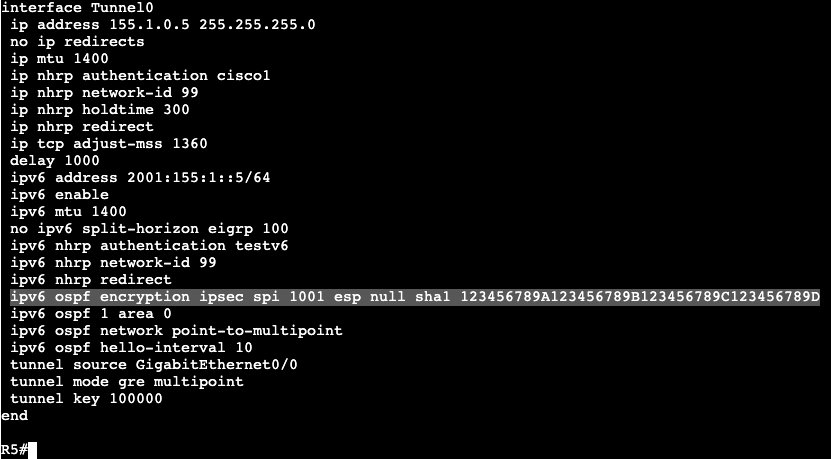
We’re going to apply an extended ACL to SVI VLAN 10 to block telnet traffic that is currently available from SW2 to SW1.
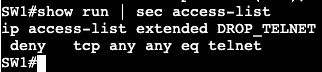
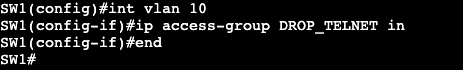
Now if we do a ‘debug ip icmp’ we’ll see that we’re administratively blocked when trying to telnet from R2 to R1.

- VLAN ACL or VLAN MAP
- Apply to an SVI
- Effective for all ports in this VLAN
- Access and Trunk Ports
- May inspect both IP and non-IP traffic
- Matching based on IP or MAC ACL
- Configuring an IP/MAC entry activates implicit deny.
- Good for impacting all future ports in VLAN.
- Don’t use implicit deny
- May block STP or ARP.
- Be careful when filtering L2 traffic.
- STP and ARP could be easily blocked.
- Account for the fact that ALL transit traffic is affected.
- Be careful when filtering transit VLANs.
- Effective for all ports in this VLAN
- Apply to an SVI
VACL Example:


Now the access-map needs to be applied to VLAN 10.

Note – When doing a VLAN access map, ICMP will not respond saying the traffic was administratively dropped like it does with a normal ACL. It quietly drops the packet.