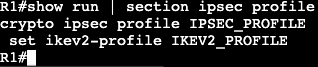
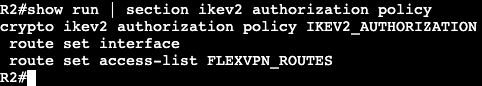
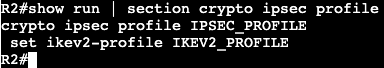
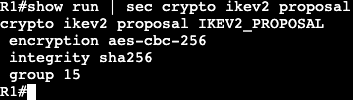
- RFC 2460 – IPv6
- Larger address space
- IPv4 – 32 bit address space
- IPv6 – 128 bit address space
- Address Types:
- Link Local
- FE80::/10
- IPv4 equivalent – 169.254.x.x
- Never routable.
- Uses:
- Stateless Address Auto-configuration (SLAAC)
- Neighbor Discovery
- Router Discovery
- Site Local
- FEC0::/10
- No one could agree on what a site is.
- Deprecated in RFC 3879
- Unique Local
- Equivalent to RFC 1918
- ‘Private’
- Likely unique but not routable over global BGP table.
- Global Unicast
- Technically everything else.
- 2000::/3
- Per RFC
- End host must have 64-bit interface ID
- Use EUI-64 format for interface ID.
- Technically everything else.
- Modified EUI-64
- RFC 4291
- Ethernet MAC to EUI-64 conversion
- Invert Universal/Local bit
- 7th most significant
- Insert padding – 0xFF 0xFE in the middle of address.
- Invert Universal/Local bit
- IPv6 Temporary Addresses
- RFC 4941
- MSDN – IPv6 identifiers
- Randomly generated interface identifiers.
- Prevents tracking users based on MAC address.
- EUI-64 result is always the same for a given MAC address.
- IPv6 Address Resolution
- RFC 4861
- ICMPv6 neighbor discovery for layer 3 to layer 2 resolution.
- Replacement for ARP.
- Neighbor Solicitation
- Equivalent to ARP Request.
- Neighbor Advertisement
- Equivalent of ARP reply.
- Router Solicitation
- Trying to find Gateway.
- Router Advertisement
- Use me for routing.
- Link Local

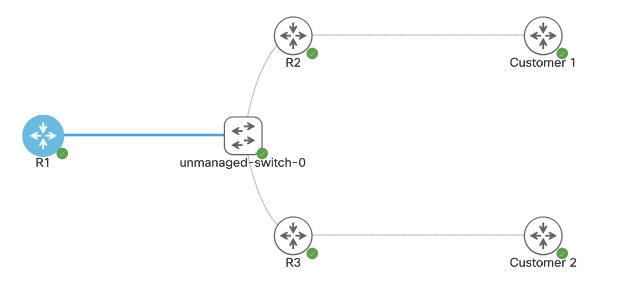
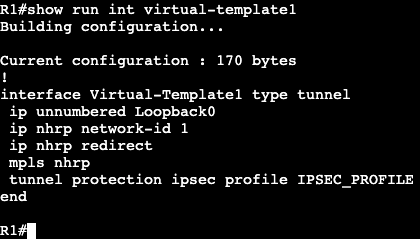
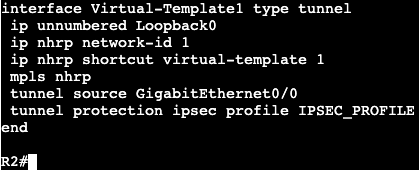
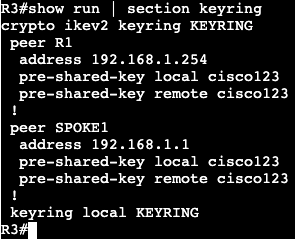
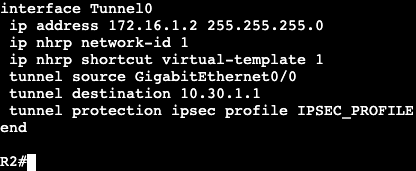
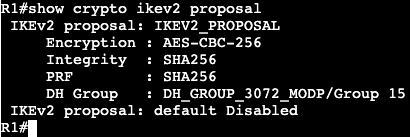
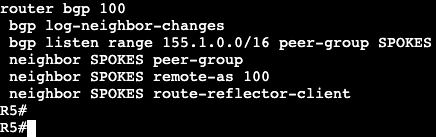
In this image we have R3 and R1 connected via both Gig0/3 interfaces. Interface configs below:

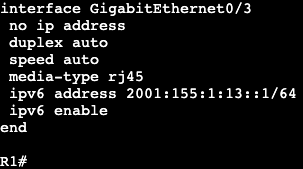
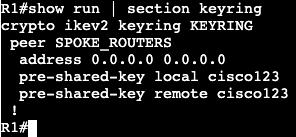
The commands ‘ipv6 enable’ and ‘ipv6 address <address>’ need to be added for unicast routing to work. In addition, the global config command ‘ipv6 unicast-routing’ needs to be entered for IPv6 to function on the box at all.
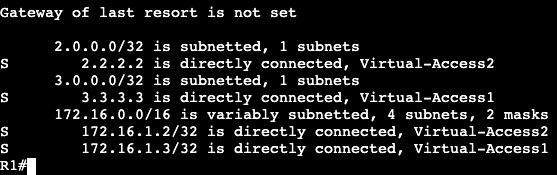
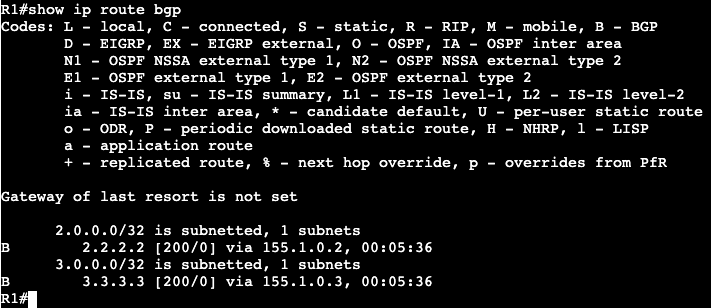
Once we successfully ping across from R1 to R3, the IPv6 neighbor table will be created. Similar to a ‘show ip arp’ in IPv4.

The table will respond with R3’s link local and global unicast address. Note- this mapping requires ICMPv6 to be enabled. If ICMPv6 is disabled, most IPv6 functionality will break with it.
SLAAC:
- Automatically assigns IPv6 address for every on-link prefix.
- Only works with /64s.
- Duplicate Address Detection (DAD) used to verify uniqueness of generated address.
- NOT DHCPv6.
- Does not include router options like DNS.
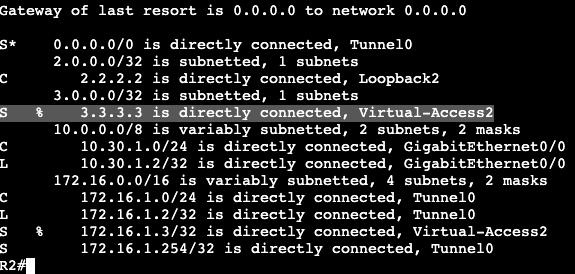
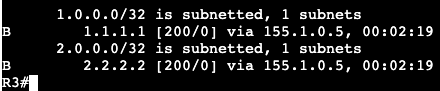
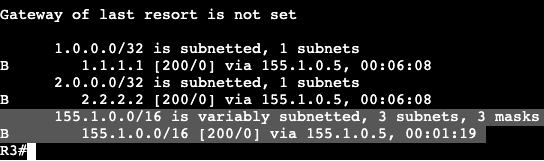
On router R1 we can add a SLAAC address to the interface gig0/3 with the command ‘ipv6 autoconfig’. That will automatically generate an address which can be seen with a ‘show ipv6 interface gig0/3’.
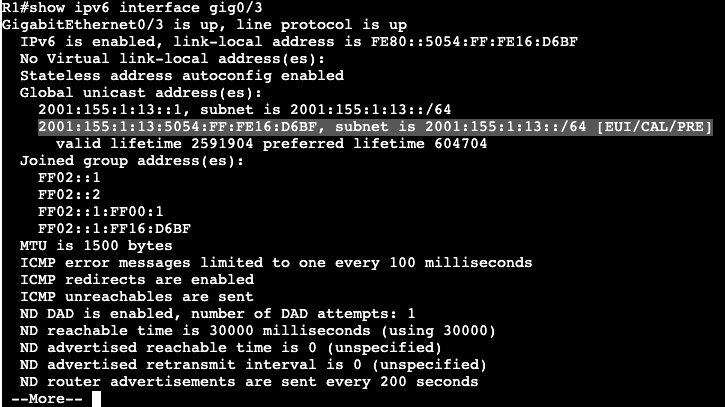
Within the address the FF:FE is found.
- SLAAC often works alongside DHCPv6.
- Options are set in RA messages
- Tells host there is DHCPv6 server available for addressing options.
- Other-Config-Flag
- Use DHCPv6 to receive just addressing options (DNS,TFTP,etc.)
- ‘ipv6 nd other-config-flag’
- Managed-Config-Flag
- Use DHCPv6 for both addressing and options.
- ‘ipv6 nd managed-config-flag’
Host Default Routing
- Hosts do not receive gateway from DHCPv6
- First hop v6 router discovered through Neighbor Discovery and Router Advertisement messages.
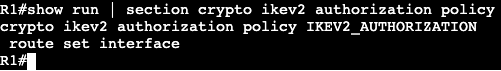
IPv6 General Prefix
- Can be defined to act as shortcut.
- e.g. if organization is assigned a /32, then all prefixes should be derived from this /32.
- helps in renumbering scenario.
- Defined globally as:
- ‘ipv6 general-prefix <NAME_OF_PREFIX> 2001:123::/32
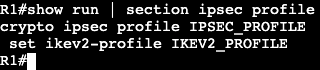
- Applied to link as
- ‘ipv6 address <Name of Prefix> ::1/64‘
- General prefix and subnet are merged to derive full address.
Global config command example:

Interface config command example:

The prefix that was added to the interface:
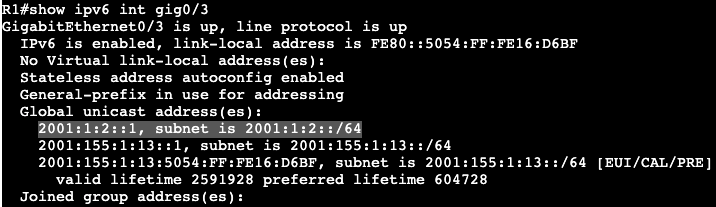
Ultimately a shortcut for assigning prefixes to interfaces.